How to Find Rogue FTP Servers & IP Addresses | JSCAPE
Learn how to secure your network & find possible rogue FTP services. JSCAPE MFT Monitor can automatically scan your network for rogue file transfer servers.

Note: This blog post was originally published on November 30, 2012 but was updated and republished on September 19, 2018.
Overview
Rogue FTP servers can be a menace. Not only do they pose a serious threat to company privacy, they can also stand in the way of regulatory compliance. In this post, you'll learn where these servers come from, what specific dangers accompany them, and how they can be detected.

How networks spring forth rogue FTP servers
First of all, FTP servers are not difficult to install. In fact, all widely used operating systems (Windows, Mac OS X, and Linux, included) already have built-in FTP servers and even FTP clients. It's just a matter of having a user with the know-how and enough administrator privileges to activate them.
Built-in FTP server on an old version of Mac OS X (Pre MacOS Mojave and High Sierra)
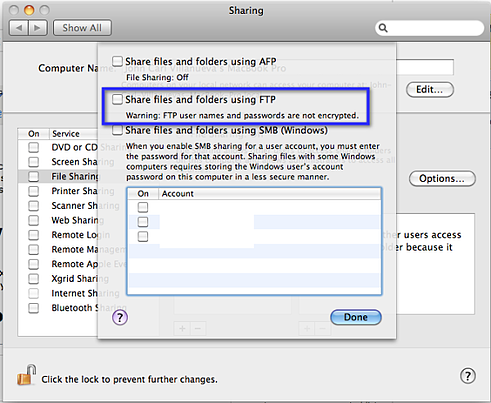
Built-in FTP Server on Windows Server 2012 R2

There are also a lot of free FTP servers and free FTP clients which can be downloaded from the Web. Obviously, anybody who wants to use FTP can easily do so. That's why FTP is often the preferred ad-hoc solution by people who need to share files.
With enough know-how, some individuals can even set up public FTP servers, which can enable them to easily share files over the Internet.
But as ad-hoc solutions, FTP servers don't usually go through the company's normal software acquisition process. They're deployed through 'shadow IT'. In other words, employees don't bother to seek approval from their IT departments (or even inform IT staff) before deploying them. Now that you know how these rogue servers come about, it's time to discuss why you wouldn't want any lying around in your network.
Dangers of having rogue FTP servers
We know that end users rarely pay attention to information security. All they're concerned with is to get their tasks done as quickly as possible. They don't bother to implement access control, authentication, authorization, encryption, and other proper security measures.
And even if these people wanted to apply security, they still lack the skills to carry out security measures effectively. Besides, deploying security tools without sufficient background on actual threats, vulnerabilities, and best practices can give users a false sense of security, which can make them even more vulnerable.
Moreso because we're talking about an ancient technology that first came into existence in the 1970's, at a time when the main motivation for developing Internet technologies was information sharing and had nothing to do with information security.
Because of FTP's inherently insecure architecture, attackers can easily carry out a number of exploits like:
-
Break into user accounts using brute force attacks; and
-
Perform bounce attacks to scan open ports, install rogue applications, execute commands maliciously, and steal files.
Let me give you one example that highlights the risks brought about by regular end users who install applications like FTP:
A tech-savvy employee named Jason wants to share files with a client. Thinking it's no big deal, Jason decides to deploy Windows' built-in FTP server on a Windows server without informing his company's IT department.
As he doesn't know what SSL is (or simply doesn't want to deal with digital certificates), Jason selects 'No SSL' during installation. As a result, the FTP server he manages to deploy is set to use plain, unencrypted FTP.
Sadly, a plain FTP connection is vulnerable to packet sniffers and man-in-the-middle attacks, which enables attackers to intercept user login credentials and in turn enable them to gain access into user accounts on the server.
As fate had it, an attack ensues and it takes some time before IT staff discover the security breach. By then, the attackers had already been long gone and the loot (confidential information consisting of employees' presonal information, financial data, and trade secrets) already passed on to the black market.
Jason had absolutely no intention of exposing confidential company data. But the data got exposed anyway.
While it may be almost impossible to stop end users like Jason (as well as those users with malicious intentions) from installing rogue FTP servers, you can certainly take steps to uncover these highly vulnerable servers before any harm is done.
How to Find Rogue FTP Servers & IP Addresses
First, you'll have to identify all file transfer servers that have been deployed by your IT department. A list of these servers will presumably be found in your inventory of services.
Once the exact location/IP addresses of these servers have been pinpointed, you can then run a scan on your network to discover any file transfer servers (FTP or otherwise) that have been deployed without your knowledge. To do perform your audit effectively, you would need a network scanning tool like JSCAPE MFT Monitor. Here's how you would use it.
Let's say you have a network that has legitimate file transfer services running on Server 1 (with IP address 172.31.35.11) and Server 2 (172.31.45.172). According to your existing inventory of services, Server 1 should only be running an SFTP service, while Server 2 should only be running a FTP/S service and an SFTP service.
.png?width=742&name=mft_monitor_scan%20(1).png)
To indicate that these services exist, you would enter them into JSCAPE MFT Monitor's list of Known Services as shown below.

You would then set up a scan that would search for certain file transfer services. In the screenshot shown below, for example, what are being searched for are FTP/S, FTPS (Implicit), and SFTP services. Under the Network section, you see that the CIDR address of 172.31.32.0/20 is entered into the IP Address field. This will instruct JSCAPE MFT Monitor to scan all possible IP addresses in the network, i.e., 172.31.32.0 - 172.31.47.255.
Alernatively, you can specify specific addresses (e.g. 172.31.35.11,172.31.45.172) if you're absolutely sure those are the only machines connected to the network.

Here's an example of how the results of such a scan looks like:

From that result, you would be able to determine what file transfer services make up your network and where they are located. We now know, for example, that a rogue FTP service is actually running on Server 1. In addition, we also now know that another rogue FTP service is actually running on an unlisted host!
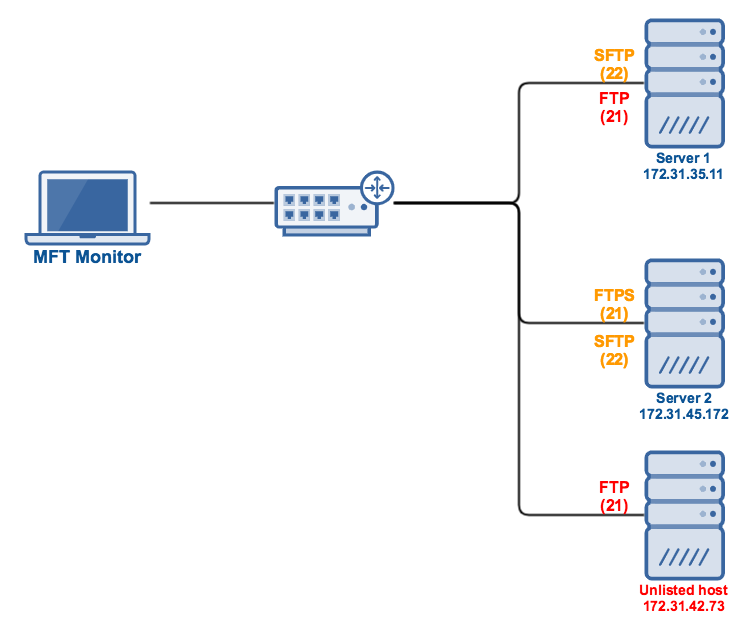
Because of these discoveries, you would be able to quickly take action and deactivate those rogue services before malicious individuals can take advantage of them. It's best if you conduct scans from time to time to prevent possible rogue servers from staying active too long.
Summary
You've just learned how rogue FTP servers come about, what dangers they bring, and how you can find them and their IP addresses. JSCAPE MFT Monitor not only scans your network for rogue file transfer servers. You can also set it up to conduct scheduled automated scans as well as to notify you when rogue servers are detected. We'll talk about those features on another blog post, so stay tuned for that.