The SSH / SFTP Key Fingerprint And Its Role In Server Authentication
The SSH/SFTP key fingerprint aids in server authentication by allowing client applications to verify the identity of the server to which they are connecting. It is a unique identifier for the server's public key, ensuring the client communicates with the intended server and not a malicious impersonator.

The first time a user connects to your SSH or SFTP server, his/her file transfer client may display an alert or notice indicating it doesn't recognize the server's fingerprint. What it's referring to is the server's SSH/SFTP key fingerprint, an important security feature that helps users and client applications authenticate SSH/SFTP servers. This post explains how it's used.
Importance of server authentication
Server authentication is a process that allows client applications to validate a server's identity. In other words, it helps a client determine whether it's connecting to the server it intended to connect to. If the server fails the SSH host key authentication process, then it's possible that the admin changed the server's host key. That's not a big problem.
However, it could also mean that someone has carried out a spoofing or man-in-the-middle attack, and the client is likely on the verge of connecting to a malicious server. Now, THAT is a serious problem.
If a user unknowingly logs in to a malicious server, whoever has control of that server could easily acquire that user's login credentials and then use those credentials to gain access to the legitimate server. Secondly, if the unwitting user uploads files to the malicious server, those files will surely fall into the wrong hands. Lastly, if a user downloads files from the server, that user could download malware.
Server authentication helps prevent these because the client will be given an appropriate warning if the authentication process fails.
SSH / SFTP server authentication using fingerprints
How do you implement server authentication in SSH/SFTP? Theoretically, you can do this. As a server admin, you can furnish each user with a copy of your server's public key. Public keys are supposed to be unique. Every time a user connects to the server, the server can show the user its public key, and the user can then compare that with his local copy. If they match, the user knows he's connecting to the right server.
There is, however, one problem with this method. Public keys are quite lengthy. So lengthy that it would be impractical for anyone to manually compare two copies. Your server authentication process will be time-consuming.
A better way of carrying out server authentication when using SSH/SFTP is by inspecting the public key fingerprint. In this context, a fingerprint is basically a hash function of a public key. Simply put, it's a shorter equivalent of the public key. If you're unfamiliar with how hashes work, I suggest you read the post "Understanding Hashing" first.
Because fingerprints are much shorter than public keys, they're also much easier to inspect and compare even through the naked eye.
How to use public key fingerprints
The first time a user connects to your SSH/SFTP server, he'll be presented with your server's fingerprint. To verify, the user can contact you, and you can then dictate your fingerprint record to him. The user can store that fingerprint for future login sessions if they match. Most SSH/SFTP clients allow users to save fingerprints.
Once a fingerprint is saved, the client can look it up whenever it connects to an SFTP server. If a match is made, the client will know it's connecting to a server it had already connected to.
It's, therefore, essential to make sure all fingerprints the client saves have already been manually verified. If you accept a fingerprint without verifying, especially if you're connecting to a remote server, you might end up storing the fingerprint of a malicious server.
It's, therefore, essential to ensure all fingerprints the client saves have already been manually verified to avoid storing the fingerprints of a malicious server. To further ensure the security of your file transfers, explore JSCAPE MFT Server. Schedule a free demo here and secure your data transfers effortlessly.
How to obtain the fingerprint if you're an administrator
What if you're an admin but don't know what your server's fingerprint is? Don't look so surprised. These things happen, you know. The quickest way to obtain it would be to log in to your SSH/SFTP server from a locally installed client application, i.e., one installed on the same machine as your server. That way, you can be sure you're safe from man-in-the-middle attacks.
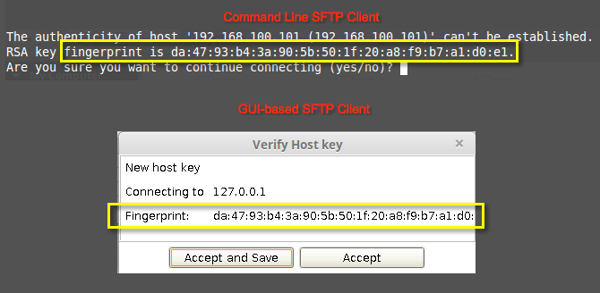
If you're using Linux and have the built-in SSH client, ensure no 'localhost' entry is found inside ~/.ssh/known_hosts file. Delete the entry if you find any before attempting the connection. The moment you connect, you'll encounter something like this:
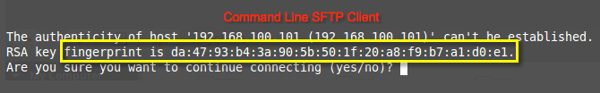
Copy that fingerprint and save it where you can easily access it.
If your server runs on Windows or another GUI-based operating system, then you can install an SFTP client like AnyClient and connect to the server (again, locally). You should then see something like this:
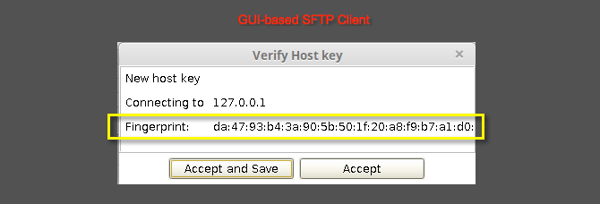
Lastly, if this tool is available on your server (it's usually available on Linux), you may run the following command:
ssh-keygen -lf /path/to/public_key/pubkey_in_openssh_format.pub
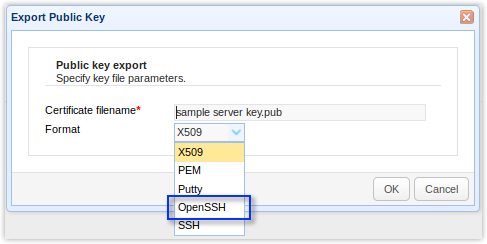
In some SFTP servers, you'll have to export the public key in OpenSSH format for this to work. In JSCAPE MFT Server, go to Server > Key Manager > Server Keys. Select the server key and click Export > Public key.
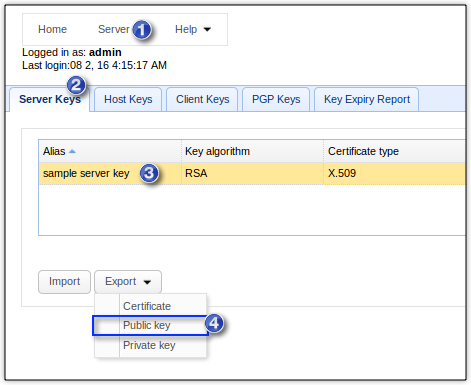
Select the OpenSSH format and then click OK.
Once the public key is exported, you can then run ssh-keygen -lf on it like so to reveal the fingerprint:
![]()
Related posts
How To Install A SFTP Server on Windows
An Overview of How Digital Certificates Work
Setting Up Public Key Authentication Between Trading Partners
Setting Up SFTP Public Key Authentication On The Command Line