What Is An SFTP Key?
An SFTP key is part of a two-factor authentication process that enhances the security of SFTP protocols by adding a layer beyond just passwords. It involves a pair of keys: a private key held by the user and a public key stored on the server. This method ensures that even if a password is compromised, unauthorized access is still prevented without the corresponding private key. SFTP keys, especially when encrypted with a passphrase, offer a robust security measure for authenticating user access to SFTP servers.

Overview
What good is an encrypted data transfer if the information it protects still falls into the wrong hands? SFTP security is best known for its ability to encrypt data in transit. But while data-in-motion encryption can secure confidential information as it traverses the network, encryption can't prevent an impostor from carrying out the download himself. For that purpose, you'll want your users to authenticate with the correct password and SFTP key.
In this post, we'll talk about the role of SFTP keys (a.k.a. private keys) in the overall security of the SFTP protocol, how it works, where to use it, and other bits of information regarding this important element of SFTP.
SFTP 2 Factor Authentication
Because of its many similarities with FTP, people who use SFTP usually treat it almost like that widely used file transfer protocol. For example, when they login to an SFTP server, they simply enter their username and password like they would with an FTP server.
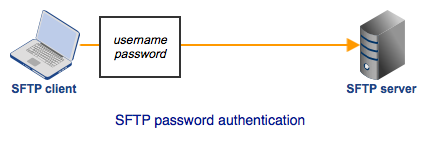
A username and password is a good method of authentication. It allows a server to authenticate a user by challenging him to submit a piece of information that (theoretically) only he - the user - would know. That information is the user's account username/password combination. Of course, we already know from the spate of celebrity hacks we encountered this year that passwords can be compromised.
Does that mean that passwords are no longer suitable for authentication? Not really. You can make password authentication work if:
1. You force your users to choose long and complex passwords and
2. You make sure their passwords are known only to them.
Still, good authentication may not be good enough. The hackers of today have already "leveled up".
So should we.
To counter more advanced attackers, you can add another layer of security to your SFTP authentication process. In addition to password authentication, which is considered one factor, you can add a second factor.
Because password authentication already challenges the user for something he knows, you can issue another kind of challenge. You can challenge the user to prove he's actually in possession of something only he should have. That something is the user's private key. An authentication process that imposes two different kinds of requirements on the user (e.g., 1. something he knows and 2. something he has) is called 2-factor authentication.
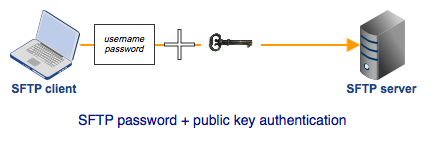
With 2-factor authentication, even if a hacker manages to guess the correct password, he would still be unable to log in successfully if he fails to use the correct private key. Note that 2-factor authentication is usually not enabled by default. You would have to enable it on the server side.
How public key authentication works
SFTP authentication using private keys is generally known as SFTP public key authentication, which entails using a public key and private key pair. The two keys are uniquely associated with one another, so no two private keys can work with the same public key.
Note: Although these public and private keys have similarities with the public and private keys used in encryption, they are used for different purposes. While the public and private keys used in encryption preserve confidentiality, the public and private keys we'll discuss here are used for authenticating a user.
To implement public/private key authentication for your SFTP service, you must generate public key/private key pairs and assign them to your users. Each key pair should be associated with one user and one user alone.
Here are 2 ways to generate an SFTP private (and public) key.
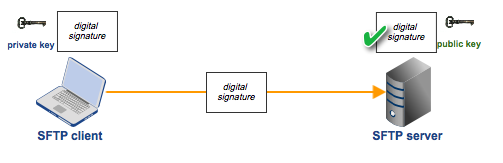
Once you've generated a key pair for a particular user, you would then place the user's public key on your server and hand over the corresponding private key to the user. The user must then keep his private key in a secret location.
Every time the user needs to log in to your SFTP server, he would have to use a capable SFTP client, enter his username and password, and then load his SFTP private key. The SFTP client will then use the private key to generate a digital signature that the server can validate and match with the user's account through the corresponding public key stored there.
Here's a screenshot showing a private key being loaded unto AnyClient, an SFTP client supporting other secure file transfer protocols.
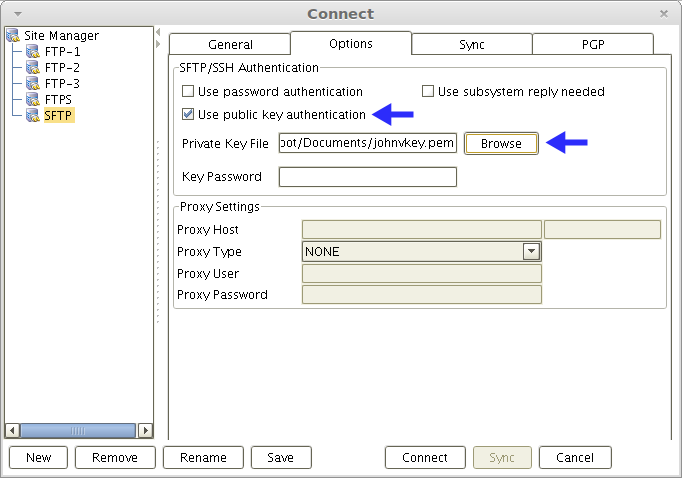
The article How To Use An SFTP Client details the steps of connecting to an SFTP server using a GUI-based client.
Securing SFTP Keys
In order for SFTP keys to serve their purpose, their owners need to keep them in secret. For additional protection, SFTP keys can be encrypted using what is known as a passphrase or key password. These are just ultra-long passwords in the form of phrases. In other words, they typically consist of more than one word. Users must remember their SFTP key's passphrase. Without it, the private key cannot be used - even by its owner!
Enhance your file transfer security with advanced authentication methods. Book a demo with one of our experts today to see how our SFTP solutions can provide the secure, two-factor authentication you need for your data transfers.
Get Started
Want to try sending files via SFTP? Download AnyClient now. It's totally free.
If you don't have an SFTP server yet, try the free, fully functional evaluation edition of the JSCAPE MFT Server.
Download JSCAPE MFT Server Trial